Methodology
How Hackers Plan and Execute Attacks: A Full Methodology Guide
Introduction
Hackers don’t just break into systems randomly. There is a structured plan, step-by-step, to find weak spots and gain access. Whether it’s to test security or cause harm, understanding this methodology is important for protecting against attacks. 🛡️
1. Reconnaissance: Gathering Information 🔍

The first stage of hacking is called reconnaissance, where hackers gather as much information 🤤 as possible about their target. This phase is like spying—the hacker learns everything they can without anyone noticing. The more they know, the easier it is to find vulnerabilities later on. Hackers will often search the web for publicly available information, such as contact details, addresses, and software used by the target. They might look at social media to discover employee names, roles, and technologies the company uses. The hacker uses tools to gather hidden data, like emails, subdomains, or server details.
Tools Used in Reconnaissance:
- Google Dorking: Hackers use advanced Google search techniques to find sensitive information that shouldn’t be publicly available. 🧐
- theHarvester: This tool collects emails, subdomains, and domain info from public sources, such as search engines and social media. 📧
- Maltego: A tool for visualizing relationships between people, organizations, and domains. 🌐
- Shodan: A search engine for finding Internet of Things (IoT) devices connected to the internet, like cameras or servers. 📡
- Recon-ng: A web reconnaissance tool that automates the process of gathering information. 🖥️
2. Scanning and Enumeration: Looking for Open Doors 🚪
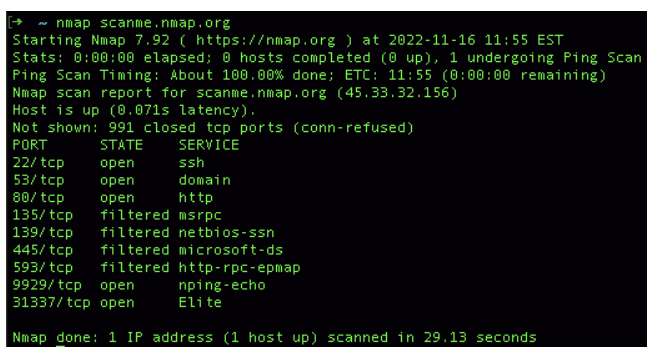
After gathering information, hackers start looking for open doors—ways to enter the target system. This phase involves scanning the target’s network and looking for vulnerabilities or services that can be exploited. Hackers scan the target’s system for open ports (like doors) and vulnerable services that can be attacked. They use enumeration to collect more detailed information, such as usernames or system configurations.
Tools Used in Scanning and Enumeration:
- Nmap: A popular tool for scanning networks to find open ports and services. 🔐
- Nikto: Scans web servers for vulnerabilities, such as outdated software or misconfigurations. 🌐
- OpenVAS: A vulnerability scanner that helps find weaknesses in systems. 🔍
- Dirb / Dirbuster: Tools used to discover hidden directories or files on a website. 🗂️
- Masscan: A faster version of Nmap used to scan large networks. ⚡
- ffuf: A fast web fuzzer used to discover hidden files and directories on websites. 🔎
3. Gaining Access: Breaking In 🔓
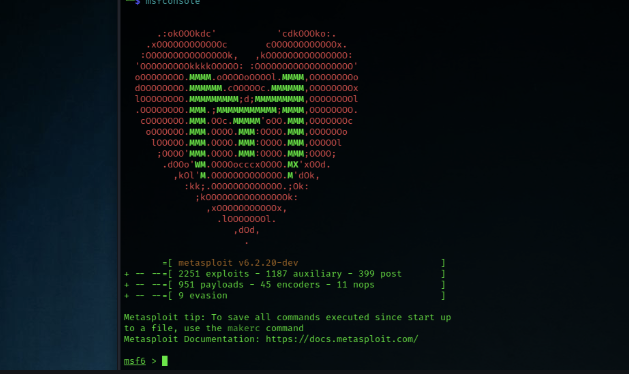
Once the hacker has found a weakness, it’s time to break in. The goal of this phase is to exploit vulnerabilities and gain control of the system, whether by using an exploit, social engineering, or password cracking. Hackers use exploits to take advantage of weaknesses in the system. They may use social engineering to trick employees into revealing passwords or personal information. If the system is password-protected, hackers might use brute-force tools to guess the correct password.
Tools Used in Gaining Access:
- Metasploit Framework: A powerful tool that contains exploits to break into systems by targeting known vulnerabilities. ⚙️
- SQLmap: Used to exploit SQL injection vulnerabilities in websites and gain access to databases. 💾
- Hydra: A password-cracking tool that tests multiple combinations to guess login credentials. 🔑
- John the Ripper: Another password-cracking tool, mainly used to decode hashed passwords. 🔓
- MSFvenom: Used to create malicious payloads that help hackers gain control once they’ve entered a system. 💣
4. Maintaining Access: Staying Inside 🛠️

What is it?
Once the hacker has broken into the system, the next step is to maintain access so they can return later if needed. This is done by installing backdoors, creating hidden accounts, or using malware to establish persistent access.
How does a hacker do it?
Hackers may create backdoors that allow them to access the system later, even if the original vulnerability is fixed. They might install remote access tools (RATs) or malware to make sure they can control the system whenever they want.
Tools Used in Maintaining Access:
- Netcat: A tool used to create backdoors, allowing hackers to maintain remote access. 🌐
- Meterpreter: A tool for post-exploitation, giving hackers full control over the system. 🎮
- Empire: A framework for maintaining access and controlling the system remotely. 🌍
- RATs (Remote Access Trojans): Malicious software that gives hackers full control over the system. 🕵️♂️
5. Covering Tracks: Hiding Evidence 🕶️
What is it?
The final phase of the attack involves covering tracks to avoid detection. Hackers do this by erasing logs, hiding evidence, and making it appear like they were never there.
How does a hacker do it?
Hackers will delete logs that record system activities to remove traces of their actions. They may use rootkits to hide their presence or change file timestamps to make it look like they didn’t access certain files. The goal is to erase all evidence of the attack so that the target doesn’t realize they’ve been compromised.
Tools Used in Covering Tracks:
- CCleaner: A tool used to clear system logs and browsing history. 🧹(miss used by hackers )
- Rootkits: Malicious tools used to hide evidence of a hack or maintain access without detection. 🛡️
- LogCleaner: A tool to edit or delete logs, hiding any traces of the hacker’s activity. 📝
- Timestomp: A tool that changes file timestamps, making it look like the hacker wasn’t there. 🕰️
Conclusion
Hacking isn’t random or chaotic—it’s a structured, methodical process. Hackers follow a clear path, from gathering information and scanning for vulnerabilities to maintaining access and covering their tracks. Understanding these steps is crucial for defending against attacks and strengthening cybersecurity. Whether you’re an ethical hacker or simply interested in how attacks work, knowledge of these phases is the first step in protecting systems and data from intruders. 🚀